Mochi's Tale
Mochi's Tale is a really cool little game that teaches you how to "find things out" through experimentation.
I found it a really helpful way to get you into the rhythm of learning rules without being told what they are in the first place.
Spoilers ahead!
The game is a series of rooms where you are challenged to navigate the character (Mochi) to the exit portal.
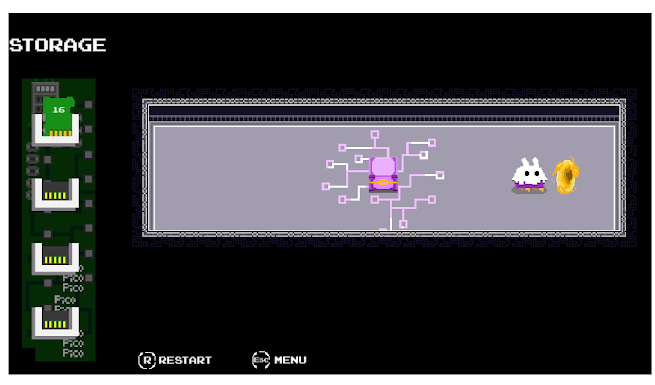
Each room has "programmable" obstacles that need to be overcome by switching values and properties.
They represented these values and properties by depicting them as removable cards.
For example, a large chest can be shrunk if you replace its size value to a smaller number.
Here the chest is size 16 and we swap it out for the card we have in storage of size 5.
This is really helpful for newbies to get the intuition that numbers and values can be transferred from one object to another.
This is how programs run inside the microchips on your computer.
Numbers are stored in slots called registers and whenever a program needs that number they'll need to look up the slot's "address" to get it.
This is useful to know for a hacker because programs like Microsoft Word come compiled as a binary executable file. This means that the source code with all its "loops" and "if" statements get reduced to a format that the computer can read.
When it's in this binary format, it's really hard to make modifications to it. Instead, we can just make the program run on our computer and tweak the values in our registers to get the result we want.
For example, the Gameboy Genie was a game cheating tool which looked at the memory of a Gameboy game while you played. It allowed you to mess with the numbers while the game was running. So you could set Mario to have 99 lives instead of 3.
Another is the MissingNo glitch in the original Pokemon games where you could increase the count of any item in your inventory. The hack goes like this: whatever item you put as the 6th item slot in your inventory, the program will add 128 to its item count. This is useful for multiplying rare items like rare candy or even masterballs.
A similar intuition is that properties can also be transferred between objects.
Here is a screenshot showing how the puzzle teaches that the colour property is also something we can modify.
The game introduces lots of properties like ghost mode, length of bridge, destroyable etc.
By looking at the "cards" that can be removed and the values that are available, the player starts to get a feel for the intuition of the environment.
Take the size of the chest and make that the length of the bridge. Transfer ghost mode to the barrier.
Having this kind of intuition is really helpful to have because it helps you treat objects as layers of usefulness rather than seeing them as all or nothing.
The game introduces a few harder and more interesting topics like loading code before its run.


Comments
Post a Comment